

This is the multi-page printable view of this section. Click here to print.




Create a Google Cloud Organization using Google Workspace or Cloud Identity
See: https://cloud.google.com/resource-manager/docs/creating-managing-organization?hl=fr
Authenticate on the Google Cloud Platform:
❯ gcloud auth login
xxxxxxxxxx
❯ gcloud organizations list
DISPLAY_NAME ID DIRECTORY_CUSTOMER_ID
xxxxxxx xxxxxx xxxxxxxx
You could find the GCP_USER:
❯ gcloud auth list
Credentialed Accounts
ACTIVE ACCOUNT
* xxxxxxxxxxxx@portefaix.xyz
Create the Service Account on bootstrap project:
❯ make -f hack/build/gcp.mk gcp-bootstrap-sa
❯ make -f hack/build/gcp.mk gcp-bootstrap-credentials
❯ make -f hack/build/gcp.mk gcp-bootstrap-iam GCP_ORG_ID=xxxx
Enable APIs on Bootstrap project:
❯ make -f hack/build/gcp.mk gcp-bootstrap-apis
Bootstrap the organization:
❯ make -f hack/build/gcp.mk gcp-organization-bootstrap GCP_ORG_ID=xxxxxxxxxxx GCP_USER=xxxxxxxxxxxxxxxxx
Then go to https://console.cloud.google.com/cloud-setup/organization to creates groups and create the billing account.
Then create the bootstrap project:
❯ make -f hack/build/gcp.mk gcp-organization-project GCP_ORG_NAME=xxxx GCP_ORG_ID=xxxxxxxxxxx
Associate this project to the Billing Account (on GCP console or using gcloud):
gcloud alpha billing accounts projects link my-project --billing-account=xxxxxxx
Then create the bucket for boostraping the organization:
❯ make -f hack/build/gcp.mk gcp-bucket GCP_ORG_NAME=xxxxxxx
Bootstrap:
❯ make terraform-apply SERVICE=terraform/gcp/root ENV=main
Terraform Cloud is used as the remote backend. Github Actions perform tasks to deploy and undeploy the GCP infrastructure.
Configure Terraform Cloud workspaces:
❯ make terraform-apply SERVICE=terraform/gcp/terraform-cloud ENV=main
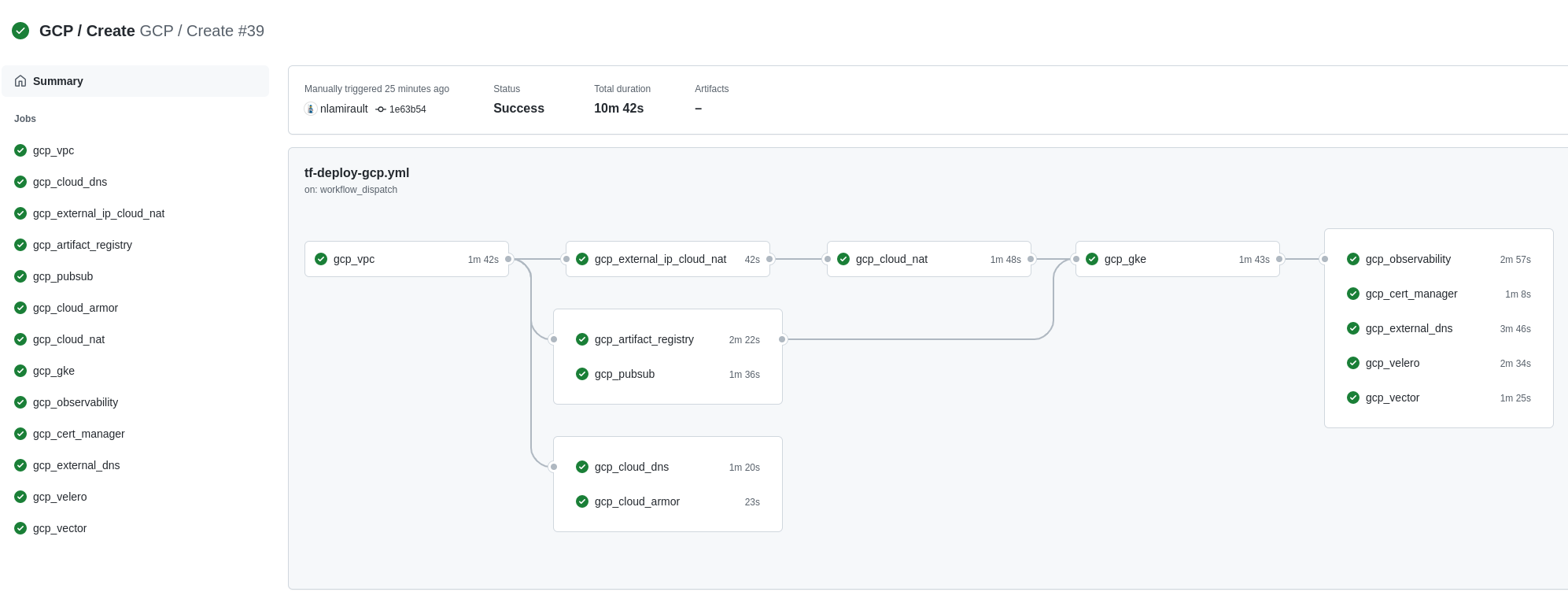
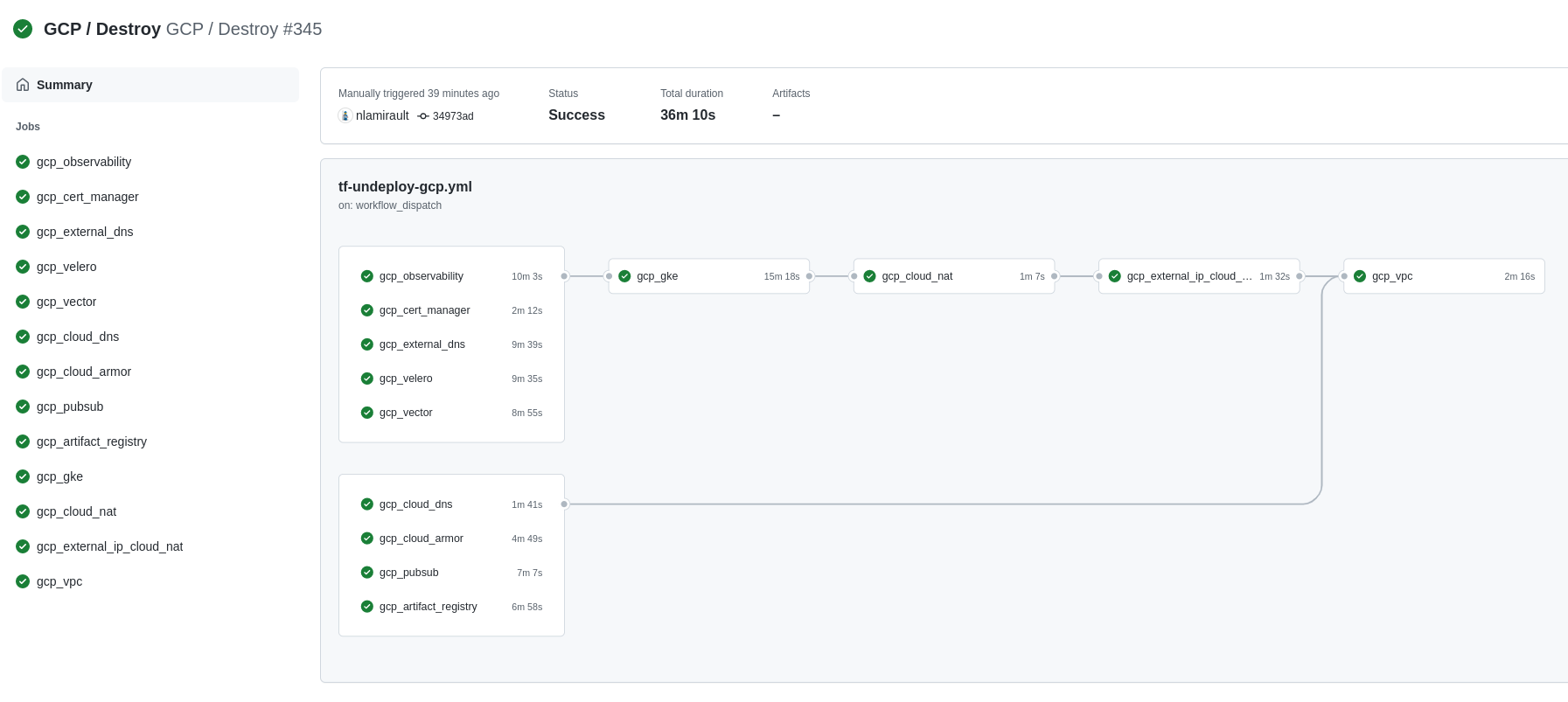
This section shows the how to setup Portefaix with authentication and authorization support in Google Cloud Platform (GCP).
To enable Cloud IAP, you need first to configure the OAuth consent screen. If you still haven’t configured the OAuth consent screen, you can do so with an email address and product name. See https://support.google.com/cloud/answer/6158849?hl=en#zippy=%2Cuser-consent
Then creates the Oauth credentials.
Select the OAuth client ID from the Create credentials drop-down list and then select web application from the
application type. Next, add a name for your OAuth client ID and click create.
❯ . ./portefaix.sh gcp
[ Portefaix ]
Setup credentials
Done
❯ make -f hack/build/azure.mk gck-kube-credentials CLOUD=gcp ENV=dev
❯ kubectl get nodes
NAME STATUS ROLES AGE VERSION
gke-xxxxxxxxxx-cluster-g-core-5d5d62be-tf15 Ready <none> 7h37m v1.18.10-gke.601
Next: Gitops
inspec is used to check infrastructure:
❯ make -f hack/build/gcp.mk inspec-debug
Test infrastructure
────────────────────────────── Platform Details ──────────────────────────────
Name: gcp
Families: cloud, api
Release: google-api-client-v0.34.1
Execute tests:
❯ make -f hack/build/gcp.mk inspec-test SERVICE=iac/gcp/<SERVICE> ENV=dev
You could upload JSON results file to Heimdall Lite to display ressults
❯ make -f hack/build/gcp.mk inspec-gcp-kubernetes ENV=dev
You could perform tests accoring the GCP CIS:
❯ make -f hack/build/gcp.mk inspec-cis ENV=dev
❯ make -f hack/build/gcp.mk inspec-test SERVICE=iac/gcp/vpc ENV=dev
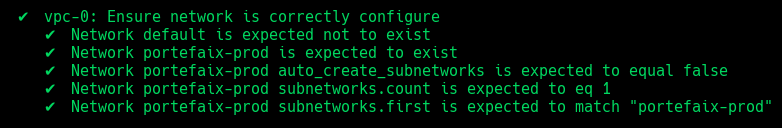
| Code | Description |
|---|---|
vpc-1 | Ensure default network is deleted |
vpc-2 | Ensure network is correctly configure |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/gke ENV=dev
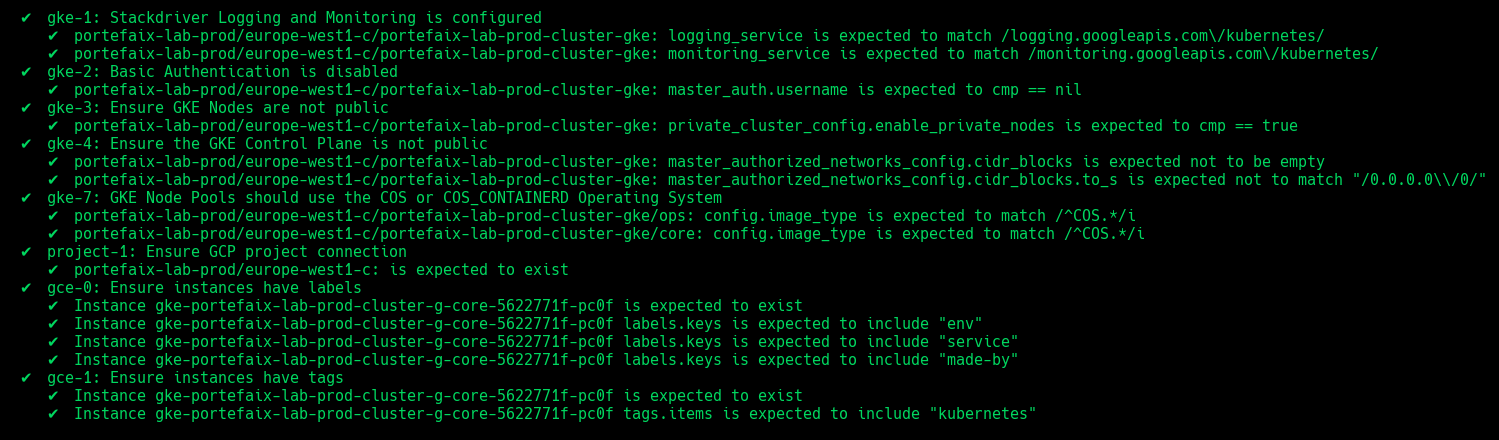
| Code | Description |
|---|---|
gke-1 | Stackdriver Logging and Monitoring is configured |
gke-2 | Basic Authentication is disabled |
gke-3 | Ensure GKE Nodes are not public |
gke-4 | Ensure the GKE Control Plane is not public |
gke-5 | Ensure the Network Policy managed addon is enabled |
gke-6 | Ensure OAuth Access Scopes and dedicated Service Accounts for node pools |
gke-7 | Ensure GKE Node Pools should use the COS or COS_CONTAINERD Operating System |
gke-8 | GKE Workload Identity should be enabled on all node pools |
gke-9 | GKE Shielded Nodes should be enabled on all NodePools |
gke-10 | Ensure instances have labels |
gke-11 | Ensure instances have tags |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/sops ENV=dev
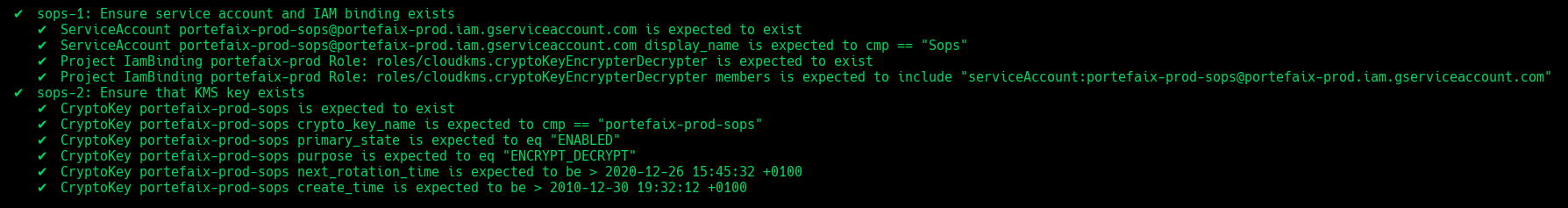
| Code | Description |
|---|---|
sops-1 | Ensure service account and IAM binding exists |
sops-2 | Ensure that Kms key exist |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/observability ENV=dev
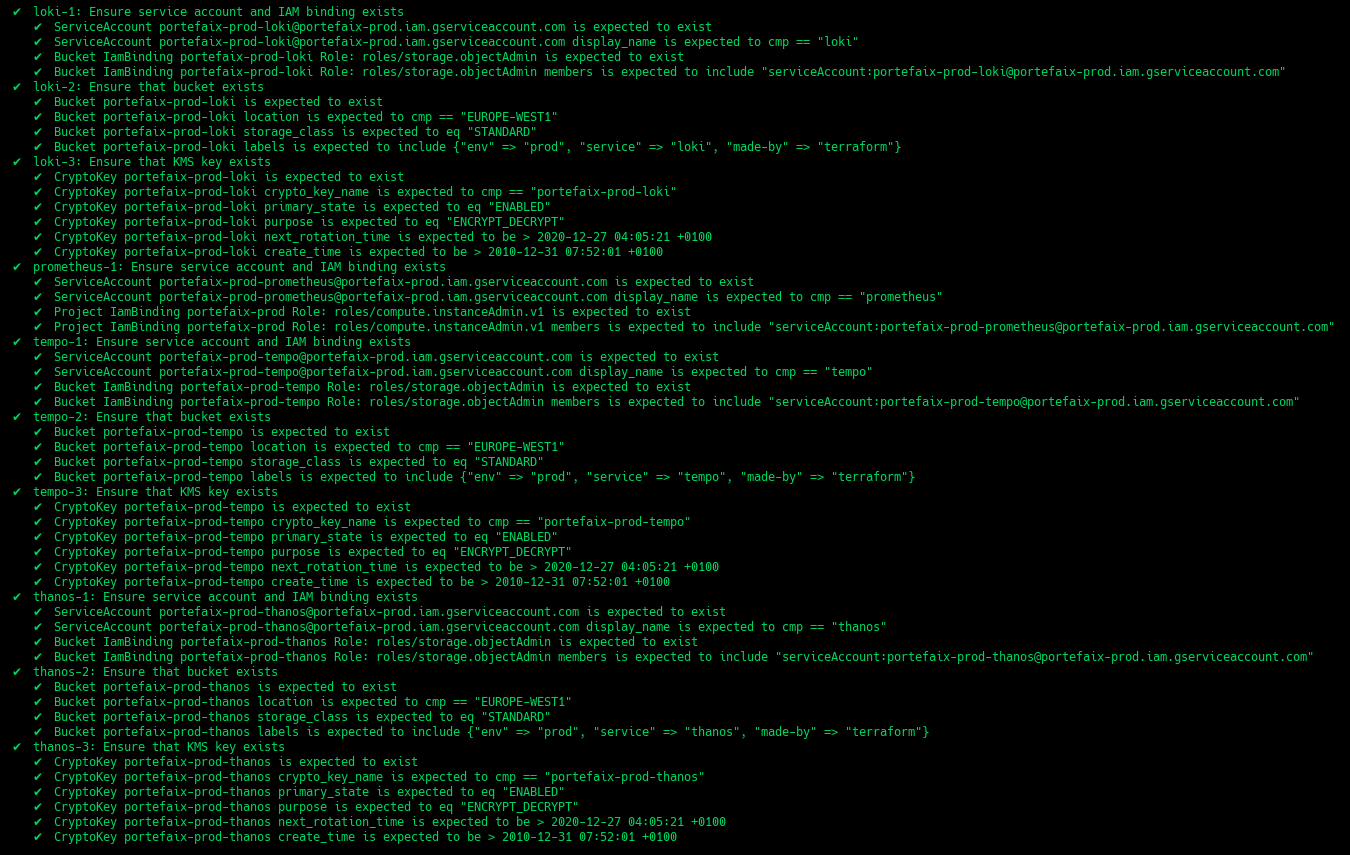
| Code | Description |
|---|---|
grafana-1 | Ensure service account and IAM binding exists |
prometheus-1 | Ensure service account and IAM binding exists |
thanos-1 | Ensure service account and IAM binding exists |
thanos-2 | Ensure that bucket exists and labels correcly set |
thanos-3 | Ensure that Kms key exist |
loki-1 | Ensure service account and IAM binding exists |
loki-2 | Ensure that bucket exists and labels correcly set |
loki-3 | Ensure that Kms key exist |
tempo-1 | Ensure service account and IAM binding exists |
tempo-2 | Ensure that bucket exists and labels correcly set |
tempo-3 | Ensure that Kms key exist |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/velero ENV=dev
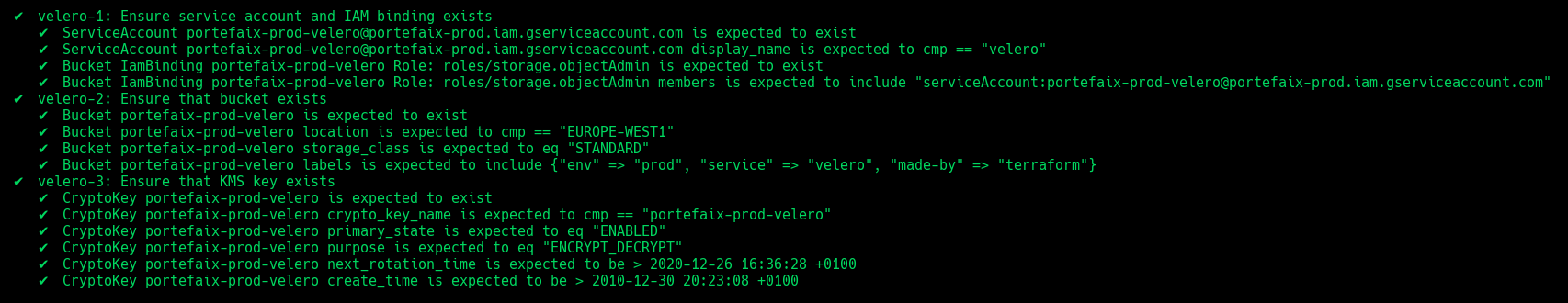
| Code | Description |
|---|---|
velero-1 | Ensure service account and IAM binding exists |
velero-2 | Ensure that bucket exists and labels correcly set |
velero-3 | Ensure that Kms key exist |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/vector ENV=dev
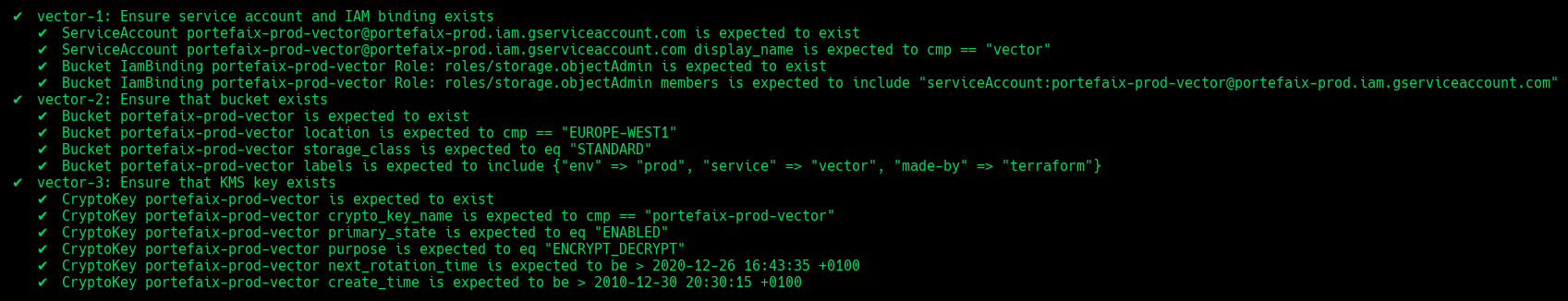
| Code | Description |
|---|---|
vector-1 | Ensure service account and IAM binding exists |
vector-2 | Ensure that bucket exists and labels correcly set |
vector-3 | Ensure that Kms key exist |
❯ make -f hack/build/gcp.mk gcp-inspec-test SERVICE=iac/gcp/external-dns ENV=dev
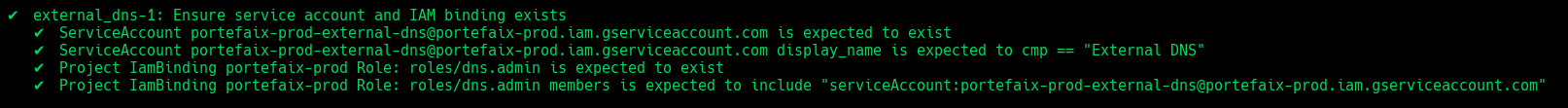
| Code | Description |
|---|---|
external_dns-1 | Ensure service account and IAM binding exists |