This is the multi-page printable view of this section. Click here to print.
Microsoft Azure
1 - Overview


2 - Install on Microsoft Azure
Setup
Export Azure credentials:
❯ export AZURE_SUBSCRIPTION_ID="xxxxxx"
create a service principal:
❯ make -f hack/build/azure.mk azure-sp
The appId, password, and tenant values are used in the next step:
export ARM_SUBSCRIPTION_ID="<azure_subscription_id>"
export ARM_TENANT_ID="<azure_subscription_tenant_id>"
export ARM_CLIENT_ID="<service_principal_appid>"
export ARM_CLIENT_SECRET="<service_principal_password>"
Storage for Terraform
Create a Storage Account :
❯ make -f hack/build/azure.mk azure-storage-account
XXXXXXXXXXX
You could see the Key on the output.
Create storage container for Terraform states:
❯ make -f hack/build/azure.mk azure-storage-container AZ_STORAGE_ACCOUNT_KEY="xxxxxxxxxxxxxxxxx"
Set permissions:
❯ make -f hack/build/azure.mk azure-permissions
Enable preview features:
❯ make -f hack/build/azure.mk azure-wasi
Terraform
Github Actions with Terraform Cloud could used to deploy and undeploy the infrastructure:
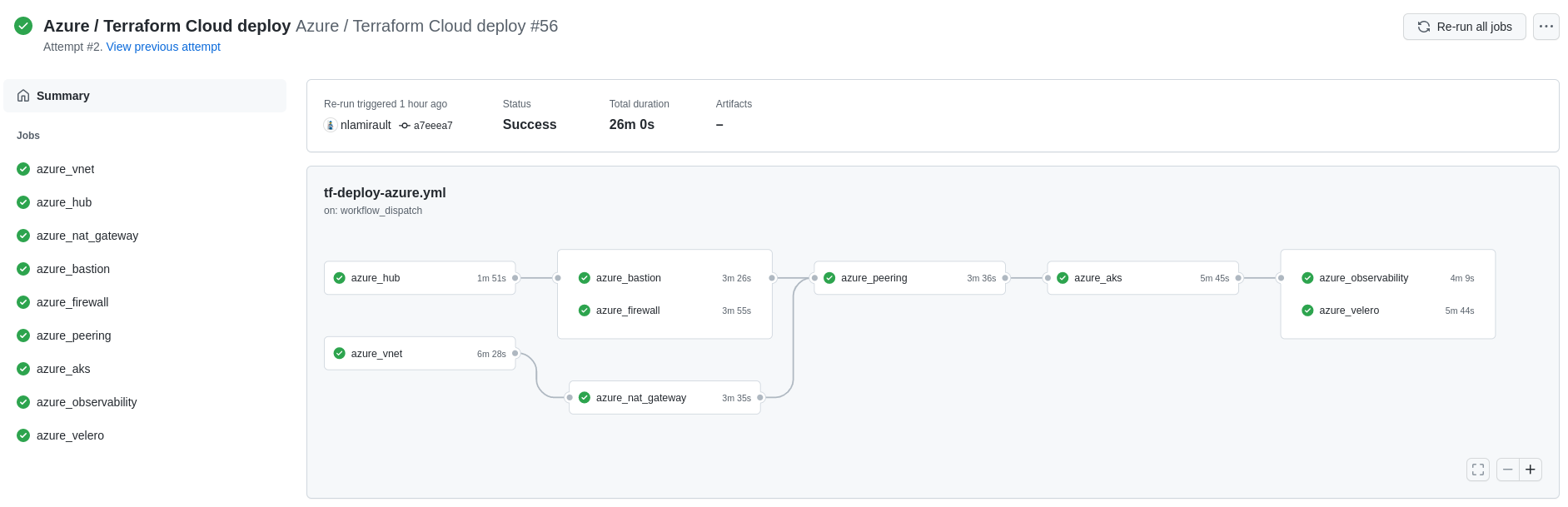
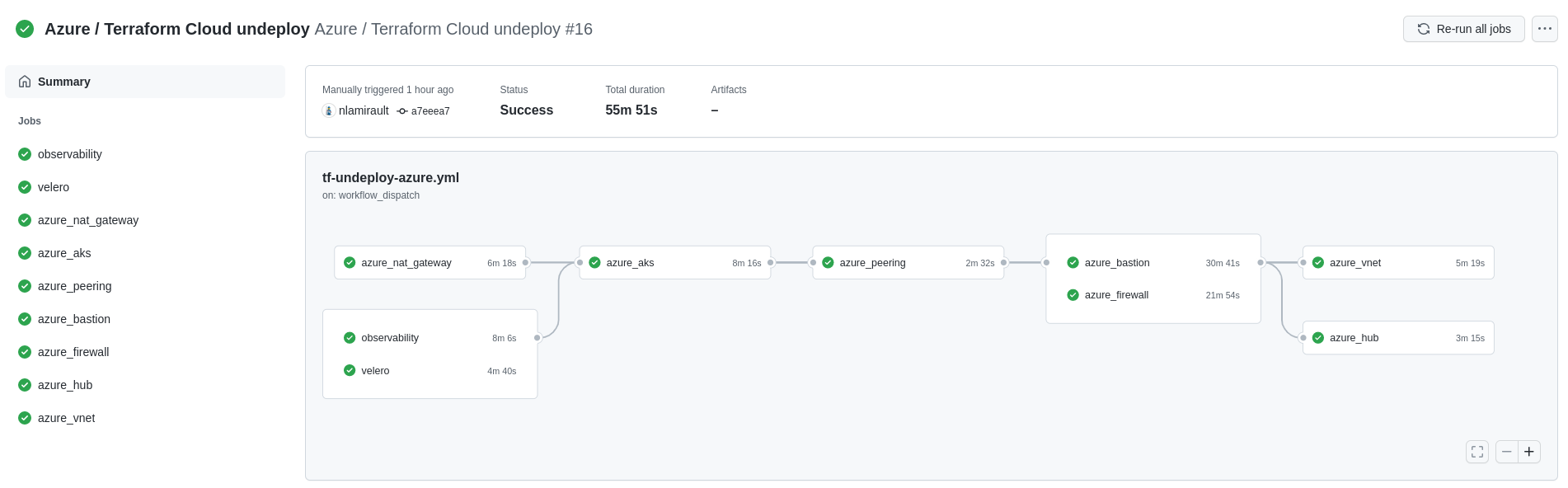
Authentication and authorization
This section shows the how to setup Portefaix with authentication and authorization support in Microsoft Azure (AZURE)
❯ . ./portefaix.sh azure
[ Portefaix ]
Setup credentials
Done
Configure kubectl
❯ make -f hack/build/azure.mk azure-kube-credentials ENV=dev
❯ kubectl get nodes
NAME STATUS ROLES AGE VERSION
aks-core-19506595-vmss000000 Ready agent 8h v1.18.10
Gitops for Kubernetes
Next: Gitops
Inspec
Setup
inspec is used to check infrastructure.
Check:
❯ make -f hack/build/azure.mk inspec-debug
Test infrastructure
────────────────────────────── Platform Details ──────────────────────────────
Name: azure
Families: cloud, api
Release: azure_mgmt_resources-v0.17.8
Execute tests:
❯ make -f hack/build/azure.mk inspec-test SERVICE=iac/azure/<SERVICE> ENV=dev
You could upload JSON results file to Heimdall Lite to display ressults
Microsoft Azure CIS Foundations
You could perform tests accoring the CIS Microsoft Azure Foundations Security Benchmark:
❯ make -f hack/build/azure.mk inspec-cis ENV=dev
AKS
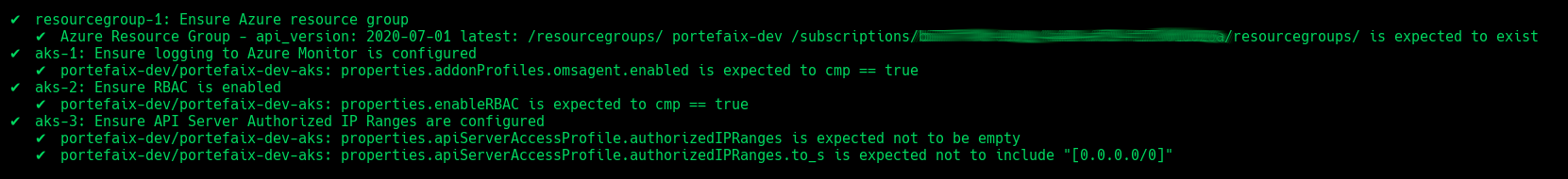
| Code | Description |
|---|---|
resourcegroup-1 | Check that resource group exists |
aks-1 | Ensure logging to Azure Monitor is configured |
aks-2 | Ensure RBAC is enabled |
aks-3 | Ensure API Server Authorized IP Ranges are configured |