Portefaix on Azure
Running Portefaix on Microsoft Azure AKS

| Name | Type | Range |
|---|
| portefaix-dev | VirtualNet | 10.0.0.0/16 |
| portefaix-dev-aks | Subnet | 10.0.0.0/20 |
| portefaix-dev-ilb | Subnet | 10.0.32.0/20 |
| ApplicationGatewaySubnet | Subnet | 10.0.64.0/24 |
| portefaix-dev-nat-gateway | Subnet | 10.0.65.0/24 |
| portefaix-dev-hub | VirtualNet | 10.10.0.0/16 |
| AzureFirewallSubnet | Subnet | 10.10.1.0/24 |
| AzureBastionSubnet | Subnet | 10.10.2.0/24 |
| PrivateLinkEndpoints | Subnet | TODO |

1 - Deployment
Instructions for deploying Portefaix on Azure
Work In Progress
1.1 - Install Portefaix
Instructions for deploying Portefaix on Azure
Setup
Export Azure credentials:
❯ export AZURE_SUBSCRIPTION_ID="xxxxxx"
create a service principal:
❯ make -f hack/build/azure.mk azure-sp
The appId, password, and tenant values are used in the next step:
export ARM_SUBSCRIPTION_ID="<azure_subscription_id>"
export ARM_TENANT_ID="<azure_subscription_tenant_id>"
export ARM_CLIENT_ID="<service_principal_appid>"
export ARM_CLIENT_SECRET="<service_principal_password>"
Create a Storage Account :
❯ make -f hack/build/azure.mk azure-storage-account
XXXXXXXXXXX
You could see the Key on the output.
Create storage container for Terraform states:
❯ make -f hack/build/azure.mk azure-storage-container AZ_STORAGE_ACCOUNT_KEY="xxxxxxxxxxxxxxxxx"
Set permissions:
❯ make -f hack/build/azure.mk azure-permissions
Enable preview features:
❯ make -f hack/build/azure.mk azure-wasi
Github Actions with Terraform Cloud could used to deploy the infrastructure:
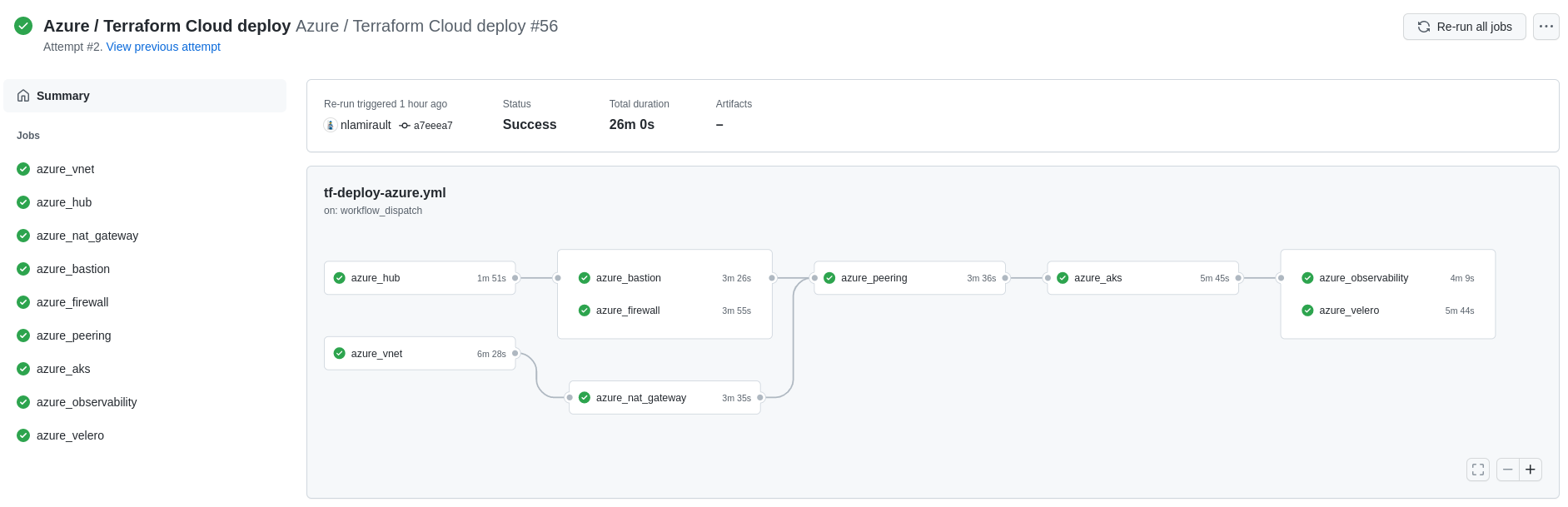
Gitops for Kubernetes
Next: Gitops
1.2 - Inspec Portefaix
Instructions for check Portefaix infrastructure on Microsoft Azure
Inspec
inspec is used to check infrastructure.
Check:
❯ make -f hack/build/azure.mk inspec-debug
Test infrastructure
────────────────────────────── Platform Details ──────────────────────────────
Name: azure
Families: cloud, api
Release: azure_mgmt_resources-v0.17.8
Execute tests:
❯ make -f hack/build/azure.mk inspec-test SERVICE=iac/azure/<SERVICE> ENV=dev
You could upload JSON results file to Heimdall Lite to display ressults
Microsoft Azure CIS Foundations
You could perform tests accoring the CIS Microsoft Azure Foundations Security Benchmark:
❯ make -f hack/build/azure.mk inspec-cis ENV=dev
AKS
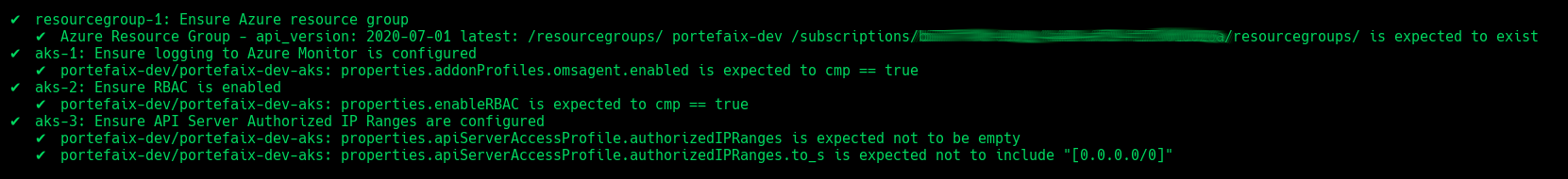
| Code | Description |
|---|
resourcegroup-1 | Check that resource group exists |
aks-1 | Ensure logging to Azure Monitor is configured |
aks-2 | Ensure RBAC is enabled |
aks-3 | Ensure API Server Authorized IP Ranges are configured |
1.3 - Uninstall Portefaix
Instructions for uninstall Portefaix
Github Actions with Terraform Cloud could be used to delete the infrastructure:
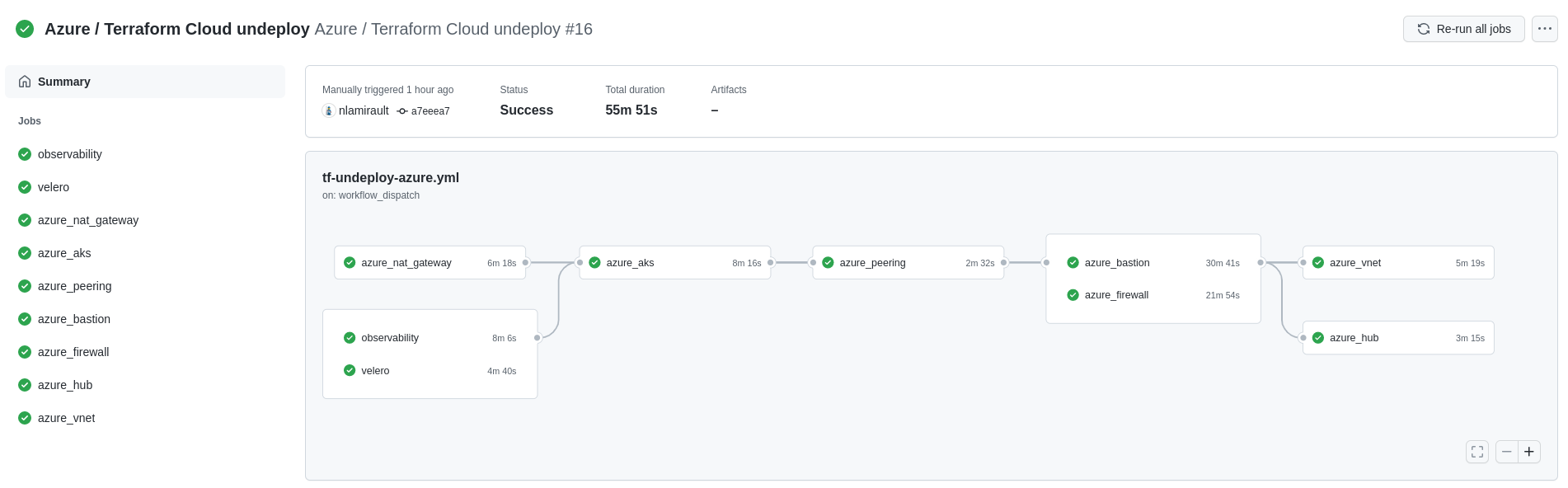
2 - Access Control for Azure Deployment
Restrict access of your deployment to specified IP addresses
This section shows the how to setup Portefaix with authentication and authorization support in Microsoft Azure (AZURE)
❯ . ./portefaix.sh azure
[ Portefaix ]
Setup credentials
Done
❯ make -f hack/build/azure.mk azure-kube-credentials ENV=dev
❯ kubectl get nodes
NAME STATUS ROLES AGE VERSION
aks-core-19506595-vmss000000 Ready agent 8h v1.18.10
3 - Troubleshooting Deployments on Azure AKS
Help diagnose and fix issues you may encounter in your Portefaix deployment




